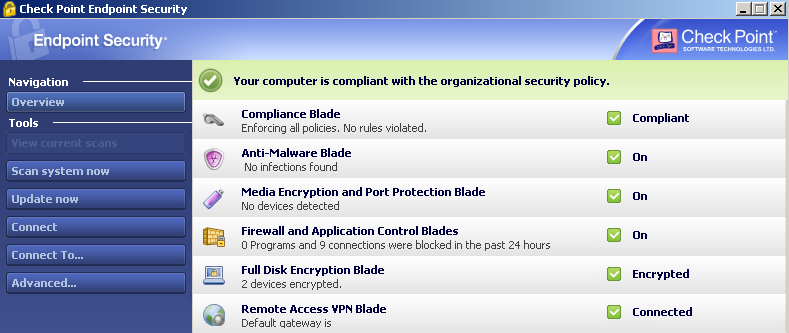
As an integrated suite endpoint security provides simple unified management and policy enforcement.
Checkpoint endpoint security review.
Buy check point advanced endpoint security online using coupon codes get discounts.
The check point endpoint security works mostly out of the box.
Then we develop an implementation plan with clear tasks responsibilities and milestones that meet your requirements for success.
Endpoint security from check point offers up a lot of functionality that can be customized for the needs of the environment.
Check point endpoint security is a single agent providing data security network security threat prevention and a remote access vpn for complete windows and mac os x security.
Test testing is a valuable opportunity to identify and mitigate any risks with the actual.
Starting at 60 per seat for the base plus 30 per.
Check point endpoint security suite including sandblast agent is an enterprise class endpoint protection suite combining antivirus and advanced threat protection full disk encryption fde remote access vdn and zero day phishing prevention among other features.
Compare features videos reviews plans and pricing specifications faqs.
Book free demo get best deals.
Check point endpoint security is ranked 12th in endpoint protection epp for business with 13 reviews while symantec end user endpoint security is ranked 1st in endpoint protection epp for business with 34 reviews.
The configuration overview is good you find what and where to configure each action very quickly.
Checkpoint is a great product.
Design we start by assigning a check point consultant to understand your security needs network environment and business goals in implementing the software blades.
The encryption excellent and the customer.
Check point sandblast agent is a complete endpoint security solution offering a fleet of advanced endpoint threat prevention capabilities so you can safely navigate today s menacing threat landscape it provides a comprehensive system to proactively prevent detect and remediate evasive malware attacks.